What is facial recognition? How does facial recognition work?
We’re here to answer those questions and give you a better understanding of this incredibly innovative technology and how to adopt it or adapt to it for your enterprise’s needs.
What is Facial Recognition?
Facial recognition is a technology that matches human faces with biometric data for identification purposes. It’s an innovative method of confirming a person’s identity using unique biometric data based on up to 80 facial nodal points.
These data points are gathered from images, videos, or real-time footage of people and are generally stored in a secure database for future retrieval.
How Facial Recognition Works
Facial recognition creates a database of facial biometric data. This data is extracted from images or videos in which facial nodes are transformed into digitized data points.
Step 1: Extract Facial Biometric Data
- A person’s face is captured in a photo or video using facial recognition technology
- Facial recognition software (such as Intelligent Video Analytics Recorder) analyzes biometric data to create a digitized and unique face profile
Capturing or uploading several images creates better facial feature extractions.
Step 2: Store Facial Biometric Data
- Facial biometric data is given a numerical value and is stored to compare against other face profiles in a database such as Gorilla Technology’s Biometric Analytics Provider
Step 3: Retrieve Facial Biometric Data for Identification
- The facial recognition system connects with the facial data to identify and confirm a face profile
- It can take up to 0.5 seconds to identify with up to 30 requests per second
Biometric data can also be used to create employee, VIP, and block lists, ensuring that only authorized people can be approved by the facial recognition system.
Key Features of Facial Recognition Systems
Most facial recognition systems can create and manage face profiles, including easy integrations to third-party systems with APIs.
Depending on the system you adopt, you could have up to 100,000 profiles with demographic data, including gender, age, and more, with an intelligent video analytics management system.
How to Get Started with Facial Recognition
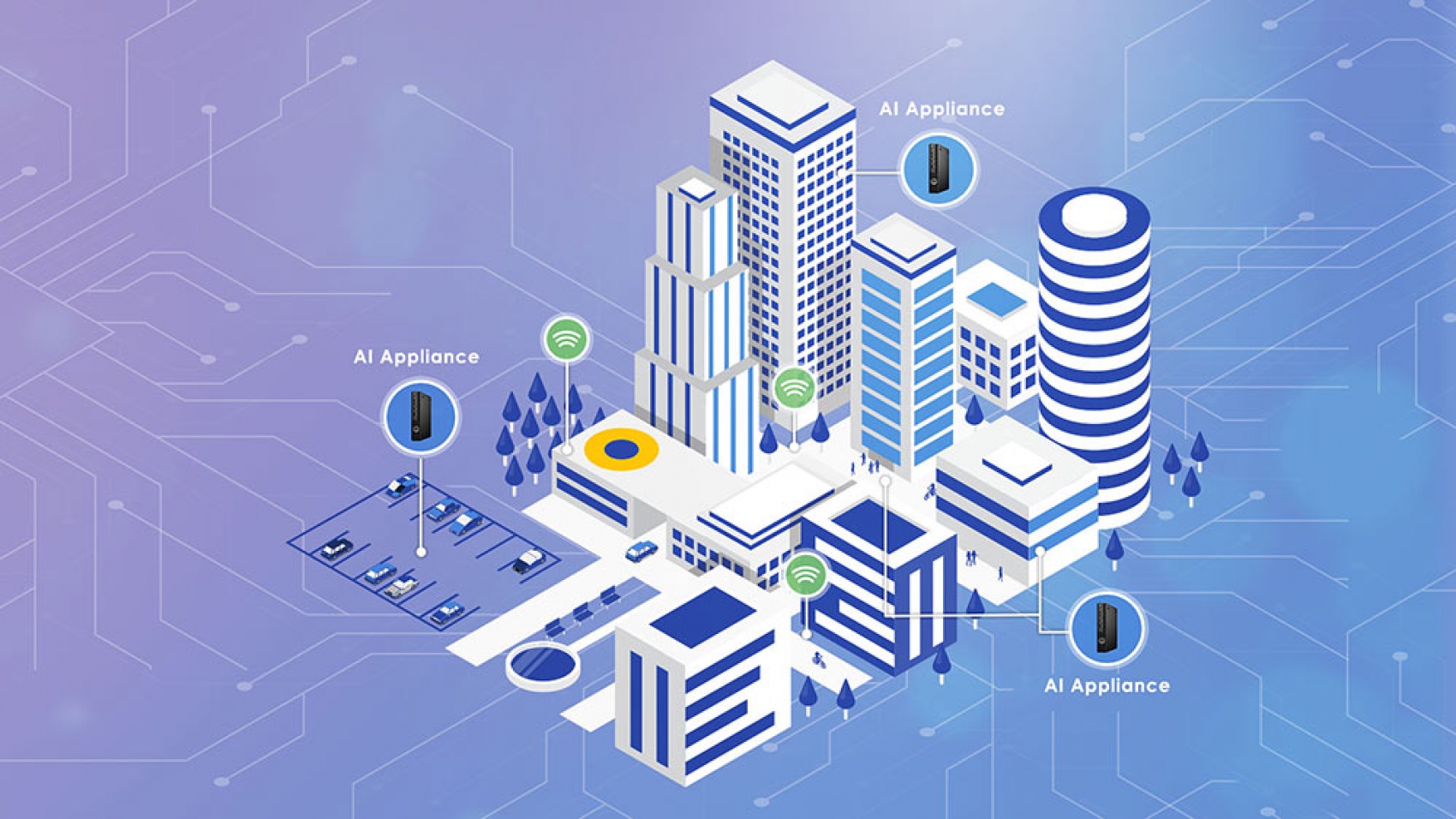
Facial Recognition requires a system that you need to build, manage, maintain, and continuously upgrade. You will need the following key components:
- Networked Cameras (to provide an image or video data)
- Server (to store and process data)
- Facial Recognition software (to analyze data)
Video management software collects videos from security cameras while biometric analytics systems analyze facial biometric data. Having these systems on a network edge will enable your business to perform faster data processing without returning biometric data back to the main server for authentication, saving valuable time.
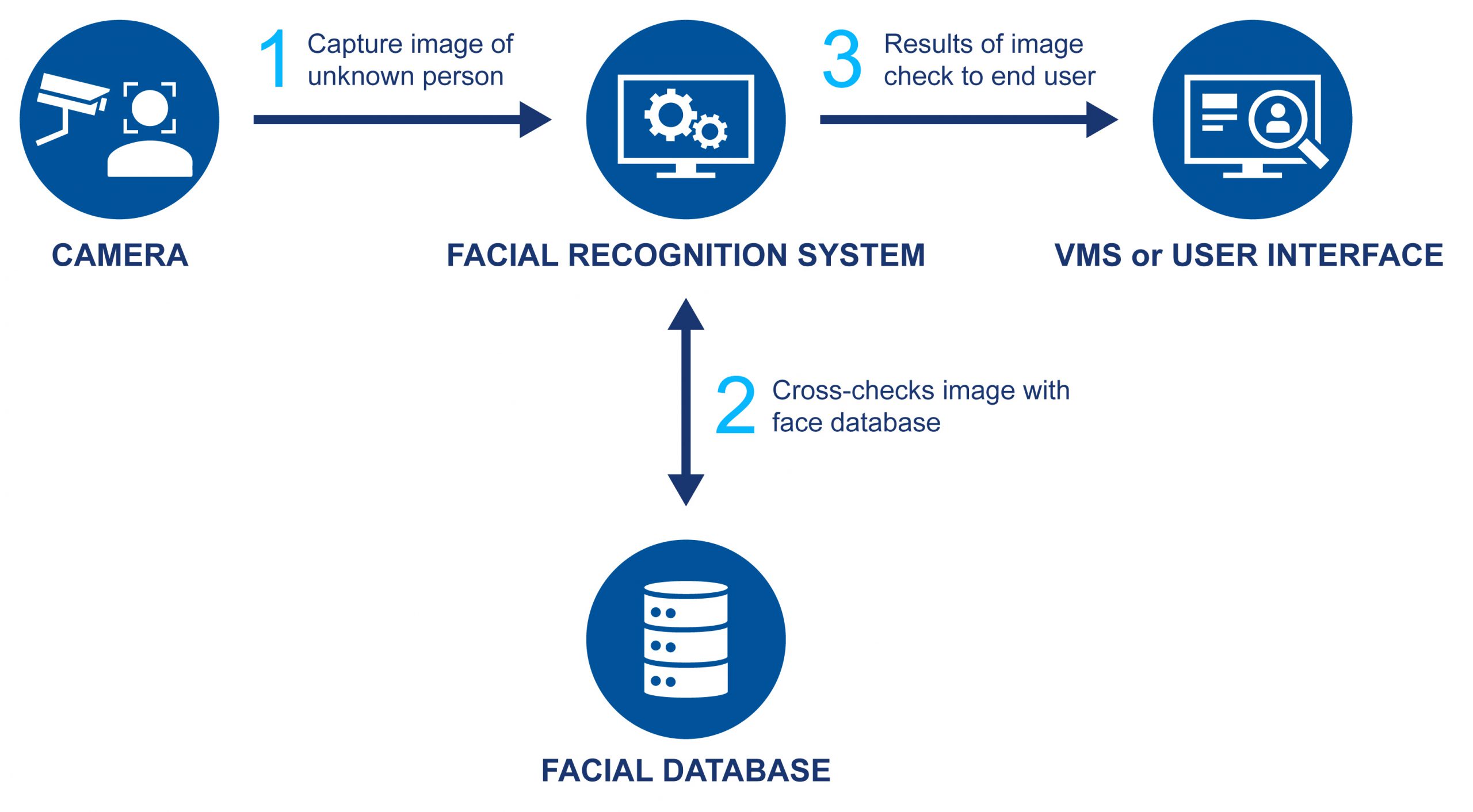
Basic Facial Recognition System Architecture
Most facial recognition systems follow a similar flow of data and processes:
The Growing Widespread Adoption of Facial Recognition
The COVID-19 pandemic increased the widespread use of facial recognition technology as a contactless form of identification. Facial recognition can also be used with other biometric security measures such as fingerprint, iris, and finger vein pattern recognition for multi-factor authentication.
However, what makes facial recognition stand out from these security measures is that:
- It’s a contactless form of identification without touchpoints
- It’s more convenient and less intrusive
- It only takes, on average, 0.5 seconds to verify a face
- It can quickly identify missing, unauthorized, and dangerous people effectively
The technology is already in wide use, and applications exist in:
- Smart Cars
- Smart Government & Public Services
- Smart Devices
- Smart City & Public Transport
- Smart Education
- Smart Retail
- Smart Healthcare
- Smart Homes
- Smart Offices
- Smart Waste Management
- Smart Ports
Facial recognition technology is a standard in our daily lives. With advances in AI and faster processors, facial recognition is a technology adopted as a new benchmark for biometric authentication.
Businesses, educational institutes, transportation hubs, and governments need effective systems to manage the flow of people.
For businesses, this could be managing employee attendance and preventing unauthorized persons from entering premises. For transportation hubs, the genuine danger of terrorism demands robust identification systems.
Gorilla Technology: A Market-leading Face Management System Solution Provider
Building facial recognition systems in-house is time-consuming, costly, difficult to maintain, and requires a high level of expertise.
That’s where Gorilla Technology’s Biometric Authentication Provider (BAP) and IVAR (Intelligent Video Analytics Recorder) come in.
Our out-of-the-box software and hardware solutions were designed with existing AI-level face recognition capabilities to identify and verify facial biometric data.
Get started and check out our video analytics software and how it can be tailored to your enterprise’s business needs, or contact our team directly to schedule a demo.